A new zero-working day vulnerability in Microsoft Office could possibly let hackers to get command of your laptop. The vulnerability can be exploited even if you never in fact open up an infected file.
Though we’re continue to ready for an formal fix, Microsoft has released a workaround for this exploit, so if you regularly use MS Office environment, be certain to examine it out.
Attention-grabbing maldoc was submitted from Belarus. It uses Word's external backlink to load the HTML and then works by using the "ms-msdt" plan to execute PowerShell code.https://t.co/hTdAfHOUx3 pic.twitter.com/rVSb02ZTwt
&mdash nao_sec (@nao_sec) Could 27, 2022
The vulnerability has been dubbed Follina by a person of the scientists who 1st looked into it — Kevin Beaumont, who also wrote a prolonged publish about it. It very first arrived to mild on Might 27 by a tweet by nao_sec, although Microsoft allegedly initial read of it as early as April. Even though no patch has been launched for it just nevertheless, Microsoft’s workaround involves disabling the Microsoft Assist Diagnostic Software (MSDT), which is how the exploit receives entry into the attacked pc.
This exploit influences mostly .rtf information, but other MS Phrase data files can also be afflicted. A aspect in MS Word termed Templates enables the plan to load and execute code from external resources. Follina relies on this in buy to enter the computer and then operates a sequence of commands that opens up MSDT. Under regular situation, MSDT is a secure software that Microsoft works by using to debug a variety of difficulties for Home windows consumers. Regretably, in this scenario, it also grants distant access to your computer, which will help the exploit take control of it.
In the scenario of .rtf documents, the exploit can operate even if you really do not open the file. As long as you check out it in File Explorer, Follina can be executed. At the time the attacker gains control of your laptop via MSDT, it is up to them as far as what they want to do. They could obtain malicious software program, leak data files, and do pretty considerably every thing else.
Beaumont has shared a good deal of illustrations of the way Follina has by now been exploited and identified in a variety of documents. The exploit is becoming used for economic extortion, amid other points. Useless to say — you never want this on your computer system.
What do you do till Microsoft releases a patch?
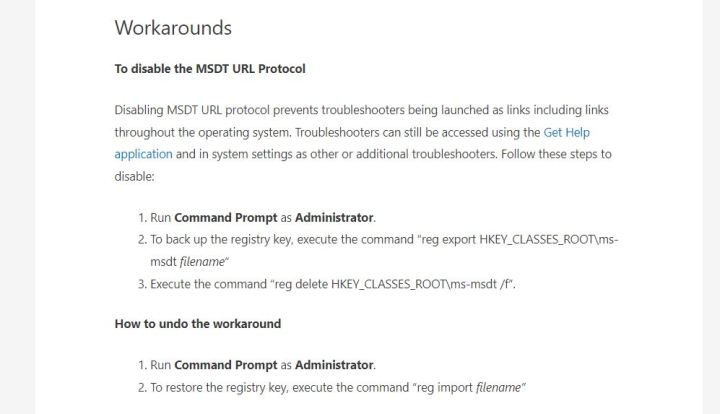
There are a several techniques you can choose to stay harmless from the Follina exploit right until Microsoft alone releases a patch that will fix this difficulty. As issues stand now, the workaround is the formal correct, and we really don’t know for a point that something else is positive to abide by.
1st and foremost, examine irrespective of whether your version of Microsoft Workplace could perhaps be affected. So considerably, the vulnerability has been observed in Business office 2013, 2016, 2019, 2021, Workplace ProPlus, and Business office 365. There is no telling whether or not more mature versions of Microsoft Business are safe and sound, nevertheless, so it’s much better to just take further methods to protect by yourself.
If you are equipped to steer clear of making use of .doc, .docx, and .rtf data files for the time currently being, it is not a poor strategy. Consider switching to cloud-primarily based alternate options like Google Docs. Only acknowledge and download information from 100%-demonstrated sources — which is a good guideline to reside by, in general.
Final but not minimum, adhere to Microsoft’s steering on disabling MSDT. It will require you to open the Command Prompt and run it as administrator, then enter a couple of entries. If every little thing goes by way of as prepared, you really should be safe from Follina. Nevertheless, don’t forget to usually be careful.
Editors’ Tips





More Stories
Quantum Space picks up speed with $15M in funding for cislunar space vehicles • TechCrunch
Tender Alerts: What They Are and How They Can Benefit Your Business
The Next Global Economic Revolution