In today’s interconnected world, cybersecurity is of utmost importance to protect the integrity and availability of online services. Among the various threats faced by organizations and individuals, Distributed Denial of Service (DDoS) attacks are a prevalent menace. This blog post aims to provide a comprehensive understanding of DDoS attacks, including their definition, impact, and potential consequences. Additionally, we will explore effective preventive measures that can be implemented to mitigate the risk of such attacks and ensure the uninterrupted operation of online systems.
Understanding DDoS Attacks:
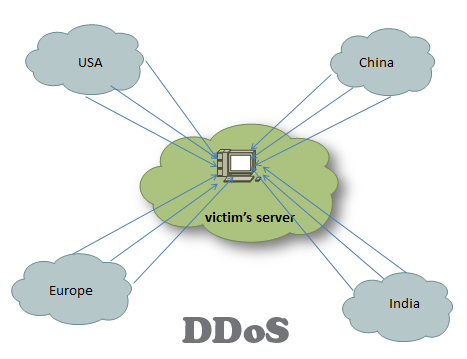
A DDoS attack is a malicious attempt to disrupt the regular functioning of a target system, such as a website or online service, by overwhelming it with a massive volume of traffic. The objective is to render the target inaccessible to legitimate users, resulting in financial losses, reputation damage, and service disruption. Unlike traditional denial-of-service attacks, DDoS attacks utilize a network of compromised devices, known as a botnet, to orchestrate the assault.
DDoS attacks come in various forms, including:
- Volume-based attacks: These floods the target with an overwhelming amount of traffic, consuming its resources. Examples include UDP floods and ICMP floods.
- Protocol attacks: These exploit weaknesses in network protocols, such as TCP/IP, to exhaust server resources. SYN floods and Ping of Death attacks fall under this category.
- Application layer attacks: These target vulnerabilities in the application layer of the target system, overwhelming it with specific requests.
Prevention Strategies for DDoS Attacks:
- DDoS Preparedness: The first step in preventing DDoS attacks is to have a well-prepared and tested incident response plan. This plan should include clear roles and responsibilities, communication channels, and escalation procedures. Conduct regular Cyber Security Training sessions to ensure that employees are aware of the risks and know how to respond effectively in case of an attack.
- Network Security Measures: Implementing robust network security measures is essential to prevent DDoS attacks. Employing firewalls, intrusion detection and prevention systems, and load balancers can help detect and filter out malicious traffic. Additionally, consider implementing rate limiting and traffic shaping mechanisms to mitigate the impact of volumetric attacks.
- Traffic Monitoring and Analysis: Utilize network monitoring tools to identify unusual patterns in network traffic. Implement real-time monitoring and analysis systems to detect and respond to DDoS attacks promptly. Anomaly detection techniques can help identify deviations from normal traffic behavior, enabling the early detection of potential attacks.
- Content Delivery Network (CDN) Services: Employing CDN services can distribute traffic across multiple servers and data centers, reducing the impact of DDoS attacks. CDNs act as a buffer between the attacker and the target, absorbing and filtering malicious traffic before it reaches the actual servers.
- Scalable Infrastructure: Designing a scalable infrastructure that can handle increased traffic during an attack is crucial. Implement load balancing mechanisms to distribute traffic efficiently across multiple servers and data centers. This ensures that the impact of a DDoS attack is minimized and that legitimate users can access the services uninterrupted.
- IP Reputation Filtering: Utilize IP reputation services and blacklisting techniques to block traffic from known malicious sources. Regularly update the lists of malicious IP addresses to enhance the effectiveness of this preventive measure.
- Cloud-Based DDoS Protection: Consider leveraging cloud-based DDoS protection services that specialize in mitigating and filtering out malicious traffic. These services have the capacity to absorb and handle large-scale attacks, ensuring the availability of online services.
- Collaboration and Information Sharing: Foster collaboration with industry peers, sharing information about emerging threats and attack techniques. By staying informed about the latest trends in DDoS attacks, organizations can proactively update their defense strategies.
Conclusion:
DDoS attacks pose a significant threat to the availability and integrity of online services. By implementing a comprehensive defense strategy that combines network security measures, traffic monitoring, and collaboration, organizations can effectively prevent and mitigate the impact of DDoS attacks, ensuring uninterrupted operations and safeguarding their digital assets.





More Stories
Powering Business Resilience: How Expert Technical Support Transforms Modern Enterprises
The Challenges of Modern Data Ecosystems Most Startups Don’t Envisage
Level Up Instantly: The Fastest Way to Buy Free Fire Diamonds in 2025